With any luck , this has helped to reassure you that It is far from possible for someone to hack your phone with just your number. On the other hand, phone hacking is a true risk and there are lots of other means for hackers to gain access.
Cover your tracks. Will not let the administrator know that the method is compromised. Do not make any changes on the website. You should not create additional data files than you would like. Tend not to create any extra users.
This commit does not belong to any department on this repository, and should belong into a fork outside of the repository.
An accidental dial happens now and then, however, if your outgoing call historical past is filled with calls you don’t keep in mind making, this could be a crimson flag. If your phone is sending out calls or texts By itself, this is a sign your phone might be hacked.
He performed video clips of himself pranking co-Doing work awaiting their food stuff, then environment off many of the pagers within a cafe at the same time.
Browse the Mac as wanted. Since you're to the user's account, you shouldn't have any restrictions as long as they have administrator privileges.
Hackers typically use this approach to connecting to devices by wireless indicates of Bluetooth as it is without doubt one of the weakest places of an android phone. Hence giving end users with the most simple solution to ways to hack an android phone using cmd.
Sending links to malicious apps. Among the list of methods that hackers hack iphone remotely kali linux will seek to hack devices is by sending links to malicious apps by way of text messages. The hacker is likely to be posing as being a respectable company offering a seemingly authentic application (photo editors and fitness trackers are typical examples).
Attackers can hazard buyers' phone security to acquire maintain of confidential data. It is dependent upon the lousy overall performance of your phone, Draining your battery, large data usage, unknown calls and texts, and unusual actions around the social manage. Here's various solutions to know that.
The computer will reboot and Visit the login screen. Once you begin to see the login screen, maintain down the Shift vital while you simply click the ability icon (the circle with a line at the top) and choose Restart. Do not carry your finger from the Shift critical until finally When you've clicked Restart!
This is without doubt one of the most accessible plus more commonly applied approaches. Normally, smartphones have a stricter safety method than PCs or servers simply because their software code prevents them from taking up the devices.
Sphinx is a well-liked spy app that lets you check someone’s phone remotely. It can be utilized to monitor calls, messages, and social media exercise, and retrieve deleted messages and information from the phone.
Create a Windows ten set up disc or travel. Make sure that you have a blank flash travel that is a minimum of 8 gigabytes in measurement (or maybe a blank writable DVD), and after that: Insert the USB flash generate or blank DVD.
Phone batteries aren’t meant to final eternally, but they’re also created proficiently. So if your phone use behavior have remained the identical but your battery is draining a lot more quickly than standard, hacking could possibly be guilty. The way to stop someone from hacking your phone
 Alicia Silverstone Then & Now!
Alicia Silverstone Then & Now! Angus T. Jones Then & Now!
Angus T. Jones Then & Now!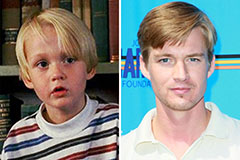 Mason Gamble Then & Now!
Mason Gamble Then & Now! Charlie Korsmo Then & Now!
Charlie Korsmo Then & Now! Andrew McCarthy Then & Now!
Andrew McCarthy Then & Now!